While preparing for a virtualized Exalytics upgrade, I was testing the various connection methods that would be needed. Last on the list was to validate that I could connect to the ILOM's web interface, launch the java console, and mount an ISO file from my laptop to the machine. This is necessary because the Oracle VM server upgrade for a virtualized Exalytics requires you to boot from a specific ISO file in order to patch the operating system. Like most patching these days, I was working remotely and noticed a new firewall rule in place that prevented me from getting to the ILOM's web console. After a long tangent trying to get console redirection to work on Linux (it's a nightmare), I thought "maybe I can just tunnel it over SSH." I had previously used the proxy tunneling method described in MOS note #1662851.1, and frequently use SSH tunneling in order to get around firewall problems.
I initially tried forwarding port 443, but that didn't get the ISO file presented. Thankfully, I came across this blog post by Enkitec's Matt Walden. It had all of the ports that I needed to get the console and ISO redirection to work flawlessly. I use a Windows virtual machine for most of my work done over VPN, so I heavily use putty. The steps to do this are:
- In the "Session" menu, enter the hostname for a host that has connectivity to the ILOM's web console. If you are planning to boot from the ISO that you're mounting, it's important to use a host *other* than the one that you are trying to reboot.
- Navigate to the Connection --> SSH --> Tunnels menu on the left hand side.
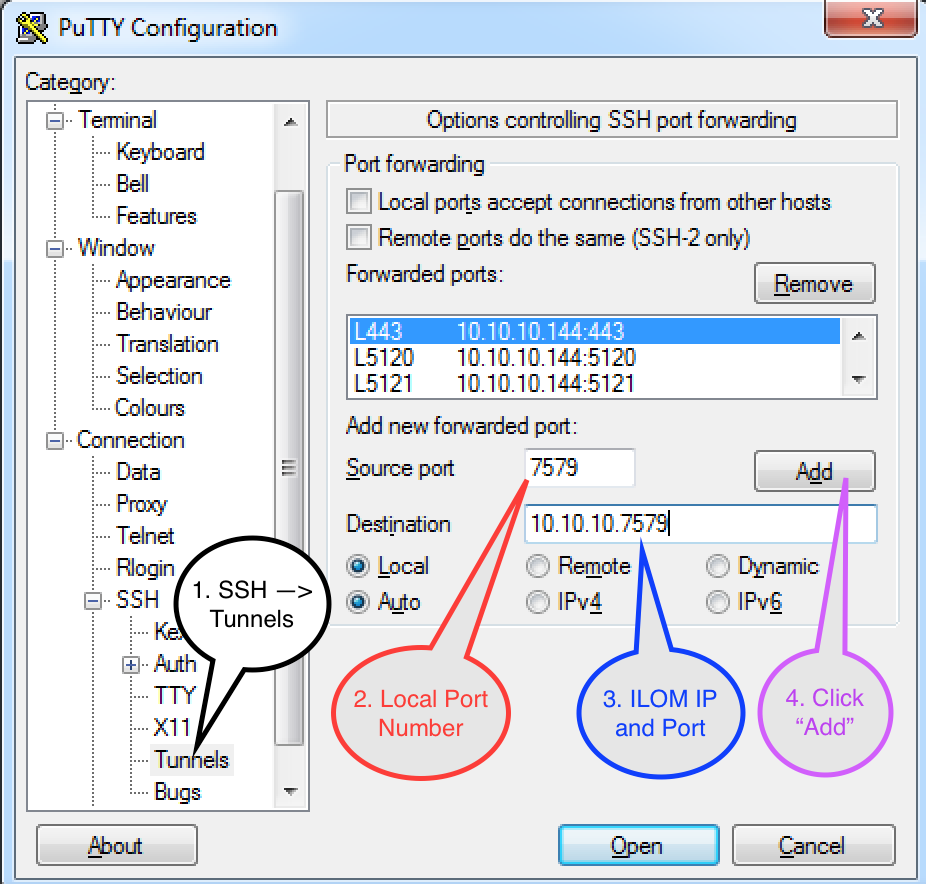
- Configure the SSH tunnels:
- Source Port - enter the port that you want forwarded. This will be the port that you hit on your machine.
- Destination - enter the IP address of the ILOM, followed by the port number on the ILOM in the following format: <IP>:<PORT>
- Leave the radio buttons set at "Local" and "Auto"
- Click "Add"
- Repeat for all of the ports that need to be forwarded. The full list can be found at the post here.
After adding the tunnel configuration, the settings should look similar to this:
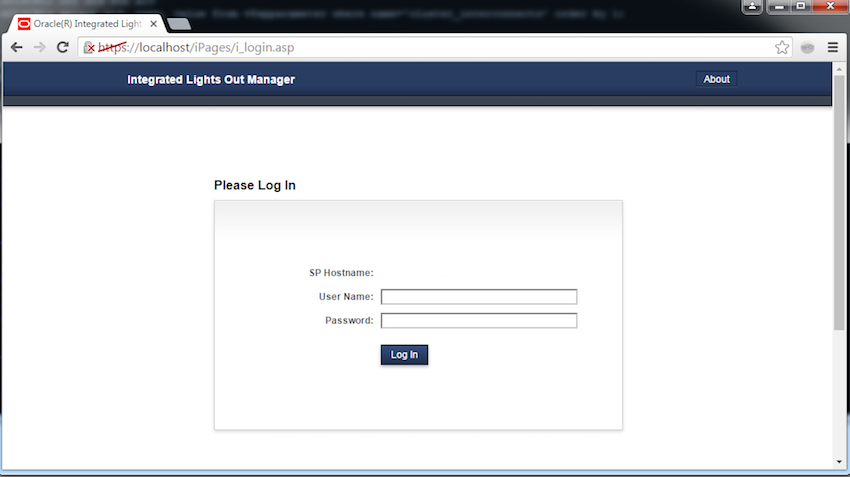
Once the tunnels have been created, click "Open" or "Apply" - the button's text depends on whether you are editing an existing session or configuring the tunnel for a new session. After you have logged in to the host, keep the window open and fire up a web browser. Now, instead of entering the hostname of the ILOM in the address bar, just type "https://localhost" and hit enter. You should get an SSL certificate warning that you can bypass, and you'll be able to log in to the ILOM's web console.
Keep in mind that this can be used for any number of applications. If you aren't tunneling through to a remote host, you can just enter "localhost:<port>" in the destination field and move along. Thanks again to Matt for having that list of ports at the ready!